Author : Altuğ AŞIK, Expert Software Engineer
The term “Advanced Persistent Threat” (APT) was used to describe state-sponsored cyberattacks designed to steal data and exploit infrastructures. Today, the term is used to describe the attacks targeted at organizations for monetary gain or espionage.
Advanced Persistent Threat is a sophisticated attack with the following characteristics:
Advanced: The techniques used to conduct the stealthy attack require advanced skills and knowledge in order to exploit the vulnerabilities of victim organization’s systems. Social engineering techniques are frequently used to attack and infiltrate the organization.
Persistent: Duration of the attack is rather long (up to months) whereas the attack involves an external command and control server that monitors and extracts data from the victim organization.
Threat: The process is managed by people rather than automated code. Organized and well-funded attackers have specific objectives and motives.
Cyber Kill-Chain
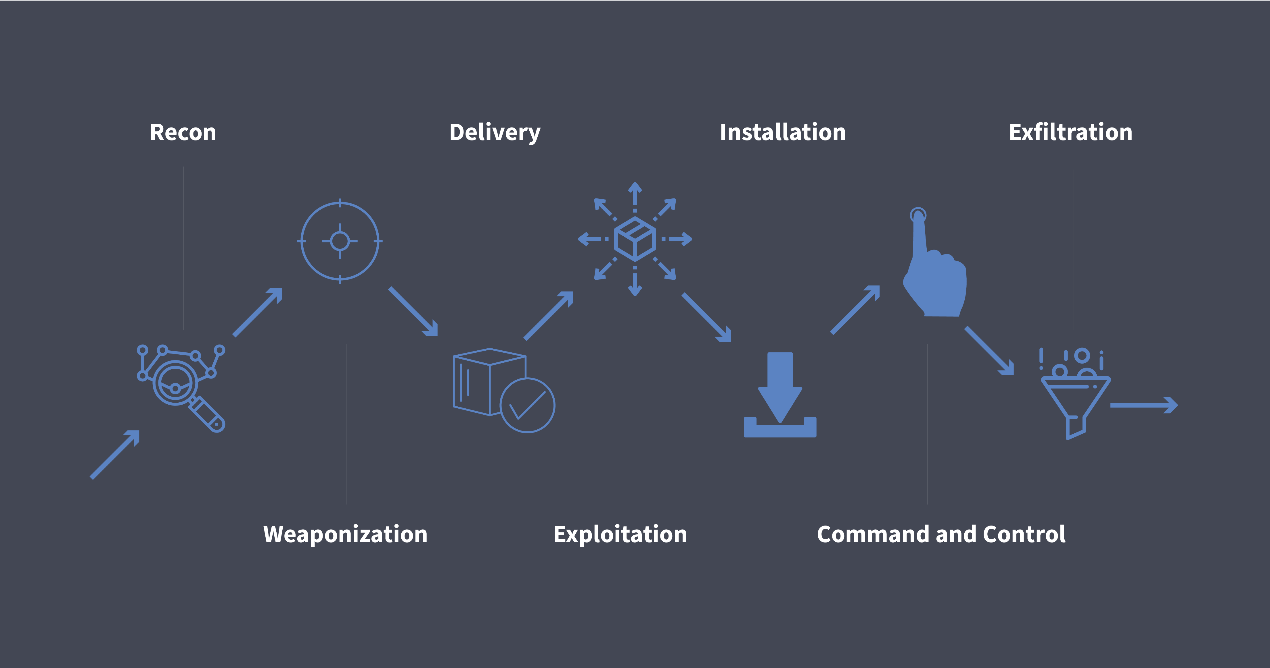
The attackers execute the following steps to carry out their vicious plans:
- Reconnaissance: Information is gathered studying targets through their public websites, following their employees on social media and using other OSINT (Open Source Intelligence) techniques.
- Weaponization: Attackers analyze the information they have gathered and determine their attack methods.
- Delivery: Delivery is accomplished through drive-by download from a website, targeted phishing attack or infection through an employee-owned device through a secure VPN.
- Exploitation: Once delivered, the malicious code is triggered to start exploiting organization’s systems.
- Installation: Once a single system is infected, the malicious activity has the potential to spread rapidly and hide its existence from security devices through a variety of methods, including tampering with security processes.
- Command and Control (C&C): To communicate and pass data back and forth, attackers set up command and control channels between infected devices and themselves.
- Exfiltration: Captured information is sent to attacker’s home base for analysis, further exploitation or fraud.
The Problem
The attack should be detected and prevented before spreading over the whole organization. Starting with the initial infection, attackers tend to leave tracks at every single step, such as malicious documents and executable files, which can be found in the filesystem or several other tracks in memory and registry in case of fileless malware attacks. Anomalies in network traffic can be detected while the attackers are communicating with their C&C servers as well. Following these tracks during the attack and employing effective protection, various attack methods can be blocked. The key is using fast, machine learning based security platforms that is trained with parameters like these tracks, as early as possible in the cyber kill chain.
The problem here is to integrate detection, prevention and removal phases of the attack. The detection process can be achieved by machine learning based platforms. However, these platforms are not smart enough to accomplish prevention and full removal of the damage yet. Experienced human security professionals are still needed for incident response and recovery.
Automation and speed is required to cope up with APT attacks. Therefore, security systems are required which are not only capable of detecting attack information in automated fashion but are also capable of using this intelligence to generate the right response to stop malicious actions before they cause substantial damage. Fully integrated automation for detection and handling is essential to enhance defense against advanced persistent threats.
Published online digital magazine: http://www.btc.co.uk/Articles/index.php?mag=Security&page=compDetails&link=9464



