Supporting our Clients with development of
Cyber Security Products and Secure Software Solutions
Core Competencies
- =Secure software development based on Common Criteria approach
- =Product security services for embedded systems, cloud and server applications
- =Software development services for Cyber Security products
- 5Flexible Intrusion Prevention System (FIPS)
- 5ICterra Honeypot System (BAKS)
- 5Edge Security And Edge Management Framework (Robust-Edge)
- 5Smart Intrusion Detection System (ATES)
Product Security Services for
Embedded Systems
- =Secure Software Development Lifecycle Implementation
- =Secure Boot
- =Secure Firmware / Software Update
- =Secure Software Execution
- =Tamper Detection
- =Embedded Firewall
- =Public Key Infrastructure (PKI)
- =Secure Data Storage
- =Custom Embedded Operating System
- =Edge Device Resource Monitoring and Management
- =Event Reporting
- =OS Hardening
Product Security Services for Cloud and
Server Applications
- =Business Requirements and Use-Cases Phase
- 5Abuse Cases Analysis
- 5Architecture Risk Analysis
- =Design Phase
- 5Threat Modeling
- 5Design Risk Analysis
- 5Design Security Review
- =Coding Phase
- 5Developer Secure Coding Trainings
- 5Secure Code Review
- 5Static / Dynamic Code Analysis
- =Testing Phase
- 5Security Test Review
- =Deployment and Maintenance Phase
- 5Penetration Test
- 5Product Security Monitoring
Integrating Security Features into the
Software Development Lifecycle according to Common Criteria Standard
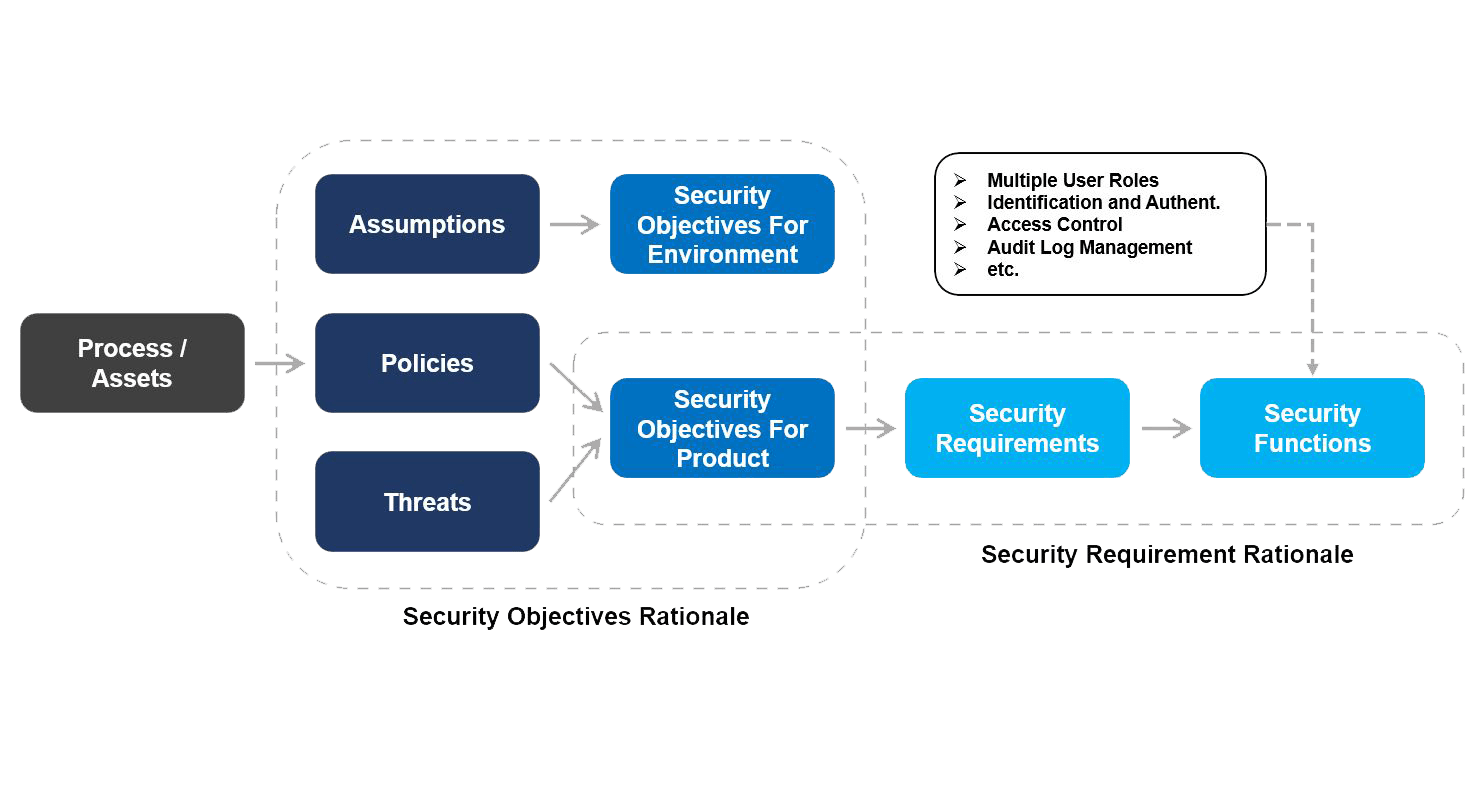
ICterra ATES (Smart Intrusion Detection System) is Common Criteria EAL 4+ certified as of September 12, 2017
Case Study
We believe your challenge will lead us to a success story.
Cyber Security
Cyber Security
Cyber Security
We share our expertise.
Secure Coding
April 08, 2021 | Security
Common Criteria provides a wealth of information about IT security
January 27, 2021 | Security
Redefining Perfection with Secure Software Development Approach
September 30, 2020 | Security
Understanding Cyber Kill Chain Model to Stop Advanced Persistent Threats
June 26, 2019 | Security
