Author: Şeref Selçuk ŞAHİN, System Architect – Cyber Security
Idle scan is a TCP based port scan where the attacker sends spoofed packets to a passive (also called as “silent”) victim host. With the term “passive” we mean here that the incoming or outgoing traffic of the victim host is very low. (The reason of this will be understood throughout the article.)
Before we go into the deeper details of the Idle Scan, two concepts have to be understood clearly:
1) IP ID
2) Response of a host to some TCP flags.
IP ID(entification) Field
IP ID is a 16-bit field in the IPv4 header which is related with IP fragmentation. We won’t dig deeper what is IP ID field in this article. But you just have known that (randomly created initial) IP ID value -mostly- will be incremented by one for each IP packet arrived to the victim host. (For more information about IP ID field: https://www.cellstream.com/intranet/reference-reading/tipsandtricks/314-the-purpose-of-the-ip-id-field-demystified.html, https://tools.ietf.org/html/rfc6864)
TCP Flags
The responses of the hosts to the SYN segments depends on the values of the flags in TCP header. To thoroughly understand the Idle Scan concept you have to know the following TCP responses.
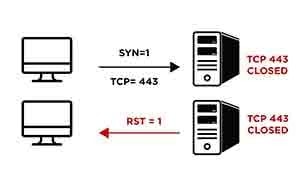
1.) If a host receives a TCP segment where SYN and ACK flags are set then it responses with the RST flag since there is no corresponding session which started with a SYN earlier to SYN/ACK)
2.) If a host receives a TCP segment to its open port where only SYN flag is set (which is describing an intent for setting up a TCP connection) then it responses with SYN and ACK flags.
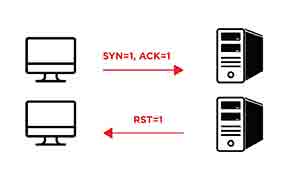
3.) If a host receives a TCP segment to its closed port where only SYN flag is set then it responses with RST flag.
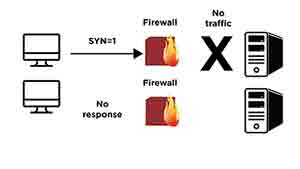
4.) If a firewall or a similar access control device blocks the access to some ports of the host then these port are called filtered ports. If a SYN segment is sent to a filtered port of the host then the host doesn’t give a response to this segment because the segment couldn’t reach the host because of the firewall which simply drops the packet. (The result is also the same for other TCP segments.)
To give a summary:
- If a SYN/ACK segment is sent to a host it responds with RST segment
- If a SYN segment is sent to a host it responds with a SYN/ACK if the port is open,
- If a SYN segment is sent to a host it responds with a RST if the port closed,
- If a SYN segment is sent to a host it doesn’t give a response if the port filtered.
After this introduction now we can proceed with the explanation of Idle Scan. We will explain Idle Scan for three different scenarios: 1) victim port open, 2) victim port closed and 3) victim port filtered. The results of Port Closed and Port Filtered scenarios are the same though.
As we mentioned above for Idle Scan to be executed we need a host of which network traffic is very low. (Or better it has almost no traffic. You can detect such idle hosts in a network with some network scanning tools.) Otherwise it can cause some false positives for the Idle Scan. Such “idle” computers generally are called as “Zombie computers”. (We also will call them as Zombie computers throughout this article.) We will use these Zombie computers to detect the status of the ports of other computers. (Seems weird. But don’t be afraid.)
After we have determined our Zombie computer in the network its time to execute Idle Scan.
Idle Scan (Victim Port Open)
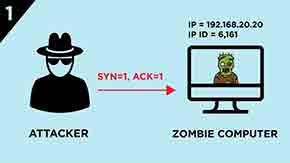
1.) The attacker sends a SYN/ACK segment to the Zombie computer.
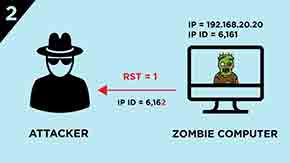
2.) Zombie computer responses with RST segment and its IP ID is incremented by “one”.
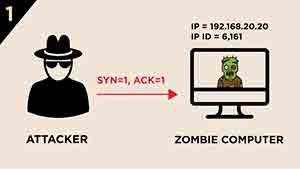
With this step the attacker learns the IP ID value of the Zombie computer which is 6,162 in this case.
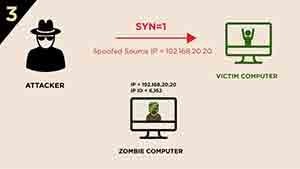
3.) After the attacker has learnt the IP ID value of the Zombie computer the attacker sends a SYN segment to the victim computer with the spoofed IP address of the Zombie computer. (Spoofed IP address is 192.168.20.20 in this case.)
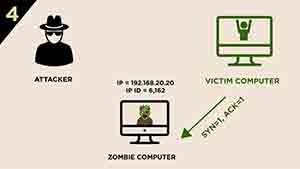
4.) Because the port on the victim computer is open then victim computer will response to the Zombie computer with a SYN/ACK Notice that the response is not sent to the attacker rather to the Zombie Computer because the attacker has spoofed the IP address of the Zombie computer.
Also be aware of that during this time period we assume that there wasn’t any traffic coming into our Zombie computer.
5.) The Zombie computer gets a SYN/ACK segment from the victim computer and the Zombie computer responds with RST segment to it and the Zombie computer increases its IP ID by “one” (IP ID = 6,163)
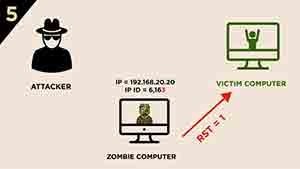
6.) The attacker sends a SYN/ACK segment to the Zombie computer.
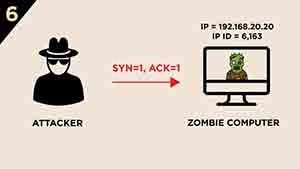
7.) The Zombie computer responds with a RST segment to the SYN/ACK segment and increases its IP ID by “one”. IP ID value will be 6,164.
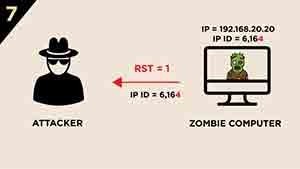
The first IP ID value of the Zombie computer sent to the attacker was 6,162. At the end of this process, the attacker gets an IP ID value of 6,164. Because the IP ID is increased by “two” we can conclude that the port of the victim computer is OPEN. As you can see we can learn the status of the ports of the victim computer via a Zombie computer with sending just a SYN segment to the victim computer. (Kinda magic, huh?)
Let me remind you the thing again: If during this time our Zombie computer sent or received any traffic from any other host then the IP ID would be increased by more than “two”. So the Idle Scan wouldn’t work for that case. That’s why it is vital that our chosen Zombie computer has to be “idle” in the network. That’s the reason where its name came from.
Idle Scan (Victim Port Closed)
As you can see below the first three phases of the Closed Port Idle Scan are the same with the first three phases of the Open Port Idle Scan.
1.) The attacker sends a SYN/ACK segment to the Zombie computer.
2.) Zombie computer responses with RST segment and its IP ID is incremented by “one”.
3.) After the attacker has learned the IP ID value of the Zombie computer the attacker sends a SYN segment to the victim computer with the spoofed IP address of the Zombie computer. (Spoofed IP address is 192.168.20.20 in this case.)
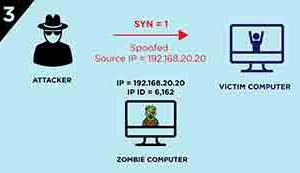
4.) Because the port on the victim computer is closed the victim computer will response to the Zombie computer with a RST Notice here also that the response is not sent to the attacker rather it is sent to the Zombie Computer because the attacker has spoofed the IP address of the Zombie computer.
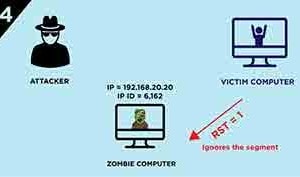
5.) The attacker sends a SYN/ACK segment to the Zombie computer.
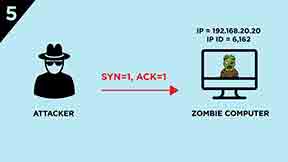
6.) The Zombie computer responds with a RST segment to the SYN/ACK segment and increases its IP ID by “one”. IP ID value will be 6,163.
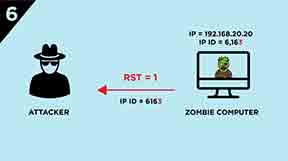
The first IP ID value of the Zombie computer which was sent to the attacker was 6,162. At the end of this process the attacker gets the IP ID value of 6,163. Because the IP ID is increased by “one” we CAN’T conclude if the port of the victim computer is CLOSED or FILTERED.
The Close Port Idle Scan and the Filtered Port Idle Scan processes yield the same result but the background processes are a little different. We will explain Filtered Port Idle Scan processes in the next section.
Idle Scan (Victim Port Filtered)
In the Filtered Port Idle Scan we assume that there is a firewall (or some other access control device) between the attacker and the Zombie computer and blocks the traffic between them.
First three steps are the same:
1.) The attacker sends a packet with SYN/ACK flags set to the Zombie computer.
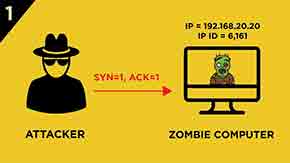
2.) Zombie computer responses with RST segment and its IP ID is incremented by “one”.
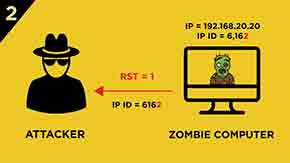
3.) After the attacker has learnt the IP ID value of the Zombie computer the attacker sends a SYN segment to the victim computer with the spoofed IP address of the Zombie computer. (Spoofed IP address is 192.168.20.20 in this case.)
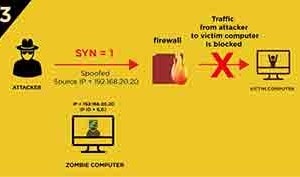
4.) The attacker sends a SYN/ACK segment to the Zombie computer.
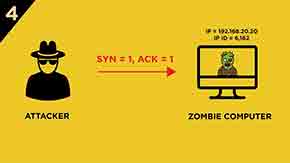
5.) The Zombie computer responds with a RST segment to the SYN/ACK segment and increases its IP ID by “one”. IP ID value will be 6,163.
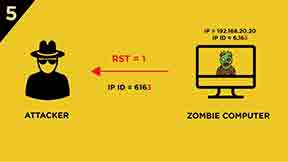
The first IP ID value of the Zombie computer which was sent to the attacker was 6,162. At the end of this process the attacker gets the IP ID value of 6,163. Because the IP ID is increased just “one” we CAN’T conclude if the port of the victim computer is CLOSED or FILTERED.
Pros and Cons
In Idle Scan if you have access to a Zombie computer which -we assume- has access to the victim computer then it is not important if there is a firewall between you and the victim computer. So with this scan the firewall is bypassed.
In Idle Scan the victim computer doesn’t see your IP address because you gather the desired information about the victim computer via and from the Zombie computer. So you are invisible for the victim computer.
With Idle Scan you can only detect the port status. Application version information detection or operating system fingerprinting is not possible with Idle Scan.
In Idle Scan, the Zombie computer -as the name implies- has to be an “idle” host which cannot be found so easy sometimes. But for example you can choose an online coffee machine connected to a network as the Zombie computer. But don’t worry the scanning tools find such coffee machines it on behalf of you.
Network scanning is in the reconnaissance phase of hacking and also called as network enumeration. There are too many scanning types to gather information about the target hosts. Nmap and nessus are free tools which are widely used for scanning networks.
References:
https://en.wikipedia.org/wiki/Idle_scan
https://nmap.org/presentations/CanSecWest03/CD_Content/idlescan_paper/idlescan.html
http://www.linux.org/threads/nmap-scanning-%E2%80%93-idle-scan.8483/



