Author: Altuğ AŞIK, Expert Software Engineer

Making software security a focal point in the process of designing, developing and delivering software applications is crucial for the ultimate success of these applications. Developing party needs to create trust in the user regarding the protection of critical assets and operational reliability. Therefore, software security becomes a fundamental requirement of software applications. Many companies started to meet software security requirements in accordance with the secure software development framework it has developed, which consists of a rule set defined within the software and security teams. This rule set are defined taking into account various international standards and industry best practices.
In the past, security-related activities were usually carried out during the testing phase and as a result, security vulnerabilities and errors were detected too late (if detected at all). The cost of removing a software vulnerability in the design phase is 30-60 times lower than the cost of removal during or after the test phase. In order to detect and reduce security vulnerabilities in the early stages and to ensure software security effectively, secure software development life cycle activities must be integrated to the software development processes.
Secure software life cycle activities that can be implemented are discussed under the following titles.
Secure Software Development Trainings
Based on the vision of “software security is everyone’s responsibility”, trainings shall be provided to all software developers and testers to improve their understanding of software vulnerability identification and mitigation techniques. These trainings aim to improve team members’ competences in defining security requirements, developing threat models and using static and dynamic code analysis tools.
Project Based Security Requirements
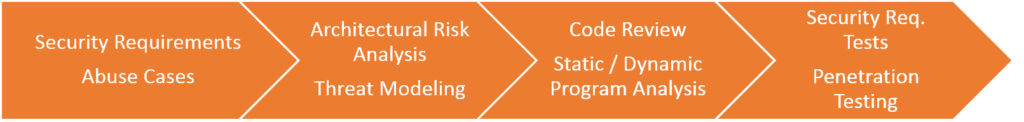
After the functional requirements of the project are determined, a two-step approach is taken to designate the security requirements. First step is developing abuse case scenarios with an attacker perspective to exploit the security vulnerabilities of the software, Second step is, defining security requirements in order to avoid these scenarios. For example, security requirements such as limiting the number of failed login attempts for the user login functionality of the software or forcing the user to set complex passwords by the software are defined in the second step. Throughout the software development process, whenever functional requirements are updated, security requirements also need to be updated.
Architectural Design Review and Threat Modeling
The cost of fixing security vulnerabilities after the implementation phase is quite high. Hence, the architectural design should be reviewed by software and security architects before the implementation phase. Security analysis of the software architecture ensures that the security-related design features are sufficiently planned.
Threat modeling activities are carried out in order to determine the security-related design features in the architectural design. Using threat modeling, security vulnerabilities are identified through evaluation of architectural features that can be exploited by different threat vectors. Then, solutions to eliminate these vulnerabilities can be determined at the design stage as well.
First stage of threat modeling activities is decomposition of the software architecture and determining how the component interfaces interact with external entities. At this stage, answer of the following question is sought: “how could a potential attacker interact with the software and the data that may be of interest to the attacker?”
Common Development Process Phases
Security Engineering
Secure Software Development Activities
Static and Dynamic Program Analysis
Using static code analysis tools integrated into the source code compilation process, it is automatically determined whether the source code contains known vulnerabilities or not. By evaluating the warning messages from the static code analysis tool, the developer can correct the source code that can cause a vulnerability.
Developers try to detect unexpected behaviors of the software by running the code with dynamic code analysis tools.
Penetration Tests
Penetration testing is carried out on the software by independent parties in order to verify the secure software development process activities before the software is delivered to users. Within the scope of penetration testing, vulnerability scanning tools are used, and various security tests are performed in accordance with attack vectors and test scenarios. Penetration tests aim to detect security vulnerabilities that may cause loss of reputation for the software product itself, user and developer organizations.
Even the full implementation of these security activities may not lead to the development of software that is perfectly secure from attackers, since attackers are constantly developing more sophisticated attack techniques. Due to the nature of software, security vulnerabilities that are not yet known by developers, which can be exploited by zero-day attacks, will exist in many software products. The main purpose of engaging in Secure Software Development Life Cycle activities is assuring the customer that the security and quality attributes of the software are verified and put into production at the highest possible level.



