Author: Fikret Ottekin, Consultant – Cyber Security

Introduction: Cyber Security and Information Security
“Cyber Security”, which gets more and more coverage on the agenda every single day, is actually a subset of information security. The weight of cyber security in information security keeps increasing due to the integration of businesses with computer networks and intensity of threat agents in the cyber space. Physical security of papers, information systems, facilities and information bearing critical human assets should still be called “information security”.
Definitions of “Cyber security”, which are available in standards and legislation are not totally consistent with each other.
For instance, Cybersecurity is defined as “preservation of confidentiality, integrity and availability of information in the Cyberspace” in ISO 27032 Guidelines for Cybersecurity [1], whereas it is defined as “Protection of information systems forming cyber space from attacks, assuring confidentiality, integrity and availability of information/data processed in this environment, detection of attacks and cyber security incidents, activation of counter-response mechanisms and recovering systems to conditions prior to the cyber security incident,” in the 2016-2019 National Cybersecurity Strategy [2]
Due to the consequences and incidents that take place in the cyber space, cyber security may also be defined as “Protection of information systems which have to work on line from the attacks conducted from the networks.”
Whether it is called cyber security or information security, all organizations should try to assure the availability and confidentiality of their business from the attacks emerging from the cyber space, with a reasonable budget. The first step towards that goal is conducting a realistic evaluation of the organization’s business, as well as the information and information systems that business depends on.
Most important objects of information security are safeguarding the availability and confidentiality of information that is generated and/or used by organizations.
In that respect, evaluation should be carried out to find out which information and information systems matter more. Value of information is related to the business where that information is used, whereas the value of business depends on contracts, expectation of economic gain, legal obligations and organizational mission and vision.
Risk Analysis
International standards evolve due to experience gained during their implementation. There are considerable differences between the 2005 and 2013 revisions of “ISO 27001 Information Security Management Systems Requirements” standard, too.
Changes indicate that “vulnerability based”, instead of “asset based” risk analysis should be conducted. I believe that correct interpretation and implementation of that change would improve the quality of both risk analysis and information security, which is the scope of this blog entry.
Two of the changes in the ISO 27001 standard is related to risk management, where the first change is about how risk analysis should be conducted and the second change is about the documentation of risk analysis:
- While the method to conduct risk analysis is defined in the 2005 revision of ISO 27001 [3]; 2013 revision simply refers risk analysis to “ISO 27005:2011 Information Security Risk Management” standard, which differs from the approach of ISO 27001:2005.
- In ISO 27001:2013, documentation of risk evaluation methodology is not mandatory any more. The requirement is rather recording the tasks practiced within the scope of risk evaluation. To sum up, “what is done” is recorded instead of “how it should be done”.
Returning to methodology, I find two statements rather significant in the latest revision of risk management standard, which clearly differ from the definitions made in the previous revisions of ISO 27001 and 27002:
- Business processes are among the primary assets of the organization [4]. They should be included in the list of assets. Yet, ISO 27002:2005 standard does not include business processes in the inventory of assets [5].
- Information security incidents may effect multiple assets [6] due to presence of assets with similar nature and vulnerabilities. Failing to manage a vulnerability that is present in multiple assets may lead to the compromise of all these assets by a threat with the capability of exploiting that vulnerability.
Evaluation of Business
The first step of preparing the inventory of assets is correctly defining the business and the business processes of the organization. Then, the value of these processes should be determined according to objective criteria. The value of a business process is proportional to the consequence that would be observed when that process comes to a halt. In terms of consequence, both material loss and loss of reputation is possible, and should be considered.
Business processes and evaluation criteria given below in Table-1, should assist all sorts of organizations and institutions:
| Type of Process | Consequence due to Process Failure |
| a. Processes running to fulfill legal obligations of the organization | Amount of sanctions defined by the legislation defining the obligation |
| b. Processes running to fulfill obligations defined by a project contract | Financial loss |
| c. Processes running to produce goods and/or services for the consumer market | Financial loss |
| d. Support processes (IT, human resources etc.) enabling the execution of the processes defined above | Total financial loss due to halt of supported processes |
Table-1. Types of processes and evaluation criteria
Evaluation of Information and Information Technology Assets
After the business processes are defined and evaluated, assets needed for the execution of these processes should be deduced.
Assets needed by a business process are as important as the business process they are facilitating. That situation may also be stated as “Assets’ value are proportional to the importance of the process that depend on them”. Hence, while assets are being evaluated, the total value of the processes those are enabled by the asset should be considered.
What’s more, just like business processes, values of software, hardware and other assets should be passed on to the assets they are dependent to [7]. Figure-1 depicts that situation.
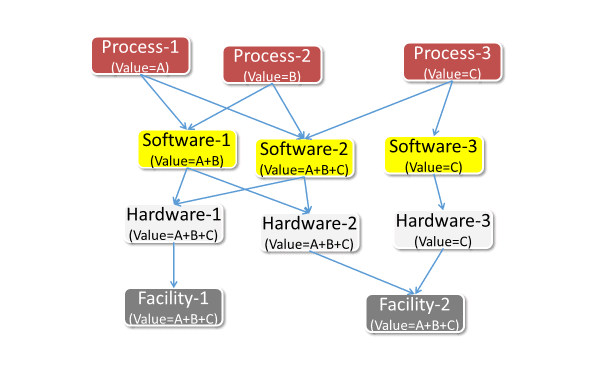
Figure-1. Evaluation of assets according to the processes they enable
Evaluation of Vulnerabilities
After the evaluation of assets, the vulnerabilities present in the assets should be reviewed.
In the context of that blog entry, “vulnerability” should be interpreted as “vulnerability of an asset due to a missing security control (such as authentication, patch management or periodic maintenance)”. That kind of vulnerability may lead to the compromise of multiple assets by a single threat agent, as stated in part 8.3.2 of ISO 27005:2011.
While conducting vulnerability analysis in an organization, implementation of a subset of the security controls that are defined in the security standards should be inquired. The subset of controls may be selected from ISO 27002, keeping in mind that the security controls should cover multiple assets or asset families.
Vulnerabilities are usually inherent to a specific kind of asset, as depicted in Figure-2.
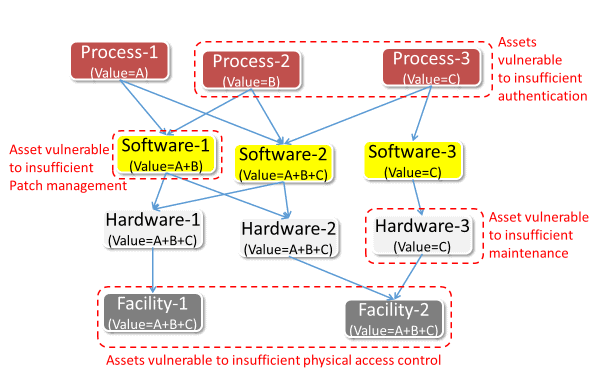
Figure-2. Vulnerabilities and effected assets
Here is a list of security controls and assets secured by that security control through successful implementation of that control. (That list may be used as a checklist to conduct vulnerability analysis in an organization):
- Secure disposal process assures confidentiality of information in printed documents and hardware, that are about to be disposed.
- Encryption measures assure confidentiality of information belonging to the organization, especially information stored in the cloud and portable memory devices.
- VPN (Virtual Private Network) assures confidentiality of information transmitted through public networks.
- Information backup process assures availability of information belonging to the organization.
- Management of environmental conditions assure availability of information systems, printed documents and the staff.
- Business continuity management assures availability of information systems, especially after natural disasters.
- Capacity management assures availability of services of human resources and information systems, especially network infrastructure and servers.
- Information security awareness assures, through staff activities, availability and confidentiality of information.
- Access control assures the confidentiality and availability of information through “need-to-know” principle.
- Network access control assures confidentiality and availability of information through network segmentation and peripheral control systems.
- Patch management assures confidentiality and availability of information accessed through COTS software applications.
- Secure software development assures confidentiality and availability of information accessed through software applications developed specially for the organization.
- Secure configuration assures confidentiality and availability of information accessed through well-known information systems, operation systems and applications.
- Antivirus systems assure confidentiality and availability of information in fixed and mobile computing environments.
- Physical access control assures confidentiality and availability of information through assuring the availability of hardware assets, especially against physical attacks, theft and sabotage.
- Inventory asset management assure confidentiality and availability of information through assuring the due coverage of all assets that are subject to security policies and practices.
- Secure maintenance process assures both availability of hardware subject to periodic maintenance (such as printers, copiers, generators, UPS, etc…) and confidentiality of information present in these devices.
- Record management assure confidentiality and availability of information through generation of evidence against unauthorized access to information systems.
- Contract management assure confidentiality and availability of information in interactions with parties providing services to the organization.
- Human resource security management assure confidentiality and availability of information available to staff, ex-staff and third parties employees authorized to access information of the organization.
- Penetration tests and security audits assure confidentiality and availability of information through reviewing and validating the current state of security controls in the organization.
Evaluation and Mitigation of Risks
The checklist given above may be used by auditors to verify each control’s implementation depth and coverage in the organization.
Reviewing the status of each security control given in the above checklist, auditors may find that
- Security control is implemented with sufficient depth and coverage.
- Security control is implemented with sufficient depth, but some of the business processes or supporting assets are not covered.
- Security control is partially implemented. Both depth and coverage is insufficient, or
- Security control is not implemented at all.
Specifying the missing depth or coverage, risks may be derived by the auditors for each security control in the checklist given above.
The following examples may be given for the risks identified in an organization with the “Solution oriented risk analysis” method:
- Since access control policy is not reviewed regularly, secret information may leak from projects specific to defense sector.
- Patch management procedure does not assure that the operating systems of users on the corporate network are up-to-date, which increases the likelihood of compromise for these computers.
- All the servers in the system room may shutdown unexpectedly since records about the periodic maintenance of UPS batteries are not available.
- Due to insufficient physical access control, sabotage or theft is not out of question for the system room at the corporate headquarters.
Examples given above clearly indicate the root cause of the risk, which is an insufficiently implemented security control.
The quantity of these risks should be assessed next. The only step that must be taken to assess the risk is deducing the likelihood that, for an (Asset Class, Vulnerability) combination, due to the presence of vulnerability, threat agents would acquire access to the assets and compromise them.
After the likelihood is deduced, quantity of the risk is computed, multiplying the likelihood with the combined value of assets defined in the risk. That is depicted in Figure-3.
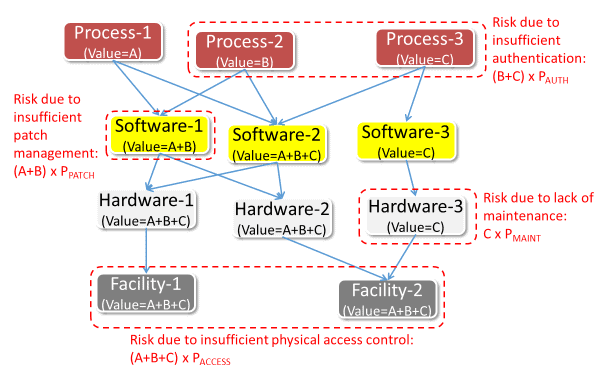
Figure-3. Risks and effected assets
Once a risk is identified and evaluated, the need to mitigate the risk should be reviewed by the management. If the risk has to be reduced and required resources are available, deciding what to do about the risk is simple, since the root cause of the risk is defined as the insufficient implementation of a security control. Implementation of that security control with sufficient depth and coverage would mitigate the risk.
Conclusion
In this blog entry, a method is defined to evaluate the business processes of an organization, the assets those are facilitating the processes and the risks that may compromise these assets.
In the defined method, risk analysis is conducted in reverse fashion, answering the question “What are the insufficiently implemented security controls in this organization?”, instead of “Which security controls should be implemented to mitigate the risks in this organization?”. In this method, the security control that should be employed to mitigate a risk is inherently present in the definition of the risk, which ease moving to risk mitigation phase from the risk evaluation phase.
The security controls that must be reviewed primarily to deduce organization’s risks is also presented as a list under “Evaluation of Vulnerabilities” heading.
References
1- «4.20 Cybersecurity,» inside ISO/IEC 27032 Guidelines for Cybersecurity, Geneva, International Organization for Standardization / International Electrotechnical Commission, 2012, p. 4.
2- «2016-2019 National Cyber Security Strategy,» [Online]. Available: http://www.udhb.gov.tr/doc/siberg/UlusalSibereng.pdf. [Accessed: 14 02 2018].
3- «4.2.1 Establish the ISMS,» inside ISO/IEC 27001 Information Security Management Systems-Requirements, Geneva, International Organization for Standardization / International Electrotechnical Commission, 2005, pp. 4-5.
4- «B.1 Examples of Asset Identification,» inside ISO/IEC 27005 Information Security Risk Management, Geneva, International Organization for Standardization / International Electrotechnical Commission, 2011, p. 33.
5- «7.1.1. Inventory of Assets,» inside ISO/IEC 17799 Code of Practice for Information Security Management, Geneva, International Organization for Standardization / International Electrotechnical Commission, 2005, p. 19.
6- «8.3.2 Assessment of Consequences,» inside ISO/IEC 27005 Information Security Risk Management, Geneva, International Organization for Standardization / International Electrotechnical Commission, 2011, p. 18.
7- T. Mataracıoğlu ve F. Ottekin, «Varlık Bağımlılıkları ve Hiyerarşik Varlık Envanteri,» Ulusal Bilgi Güvenliği Kapısı, 28 Eylül 2011.



